Add a new Server Job setting by clicking Configuration> Settings> Account management> LDAP Connections> Edit in list>

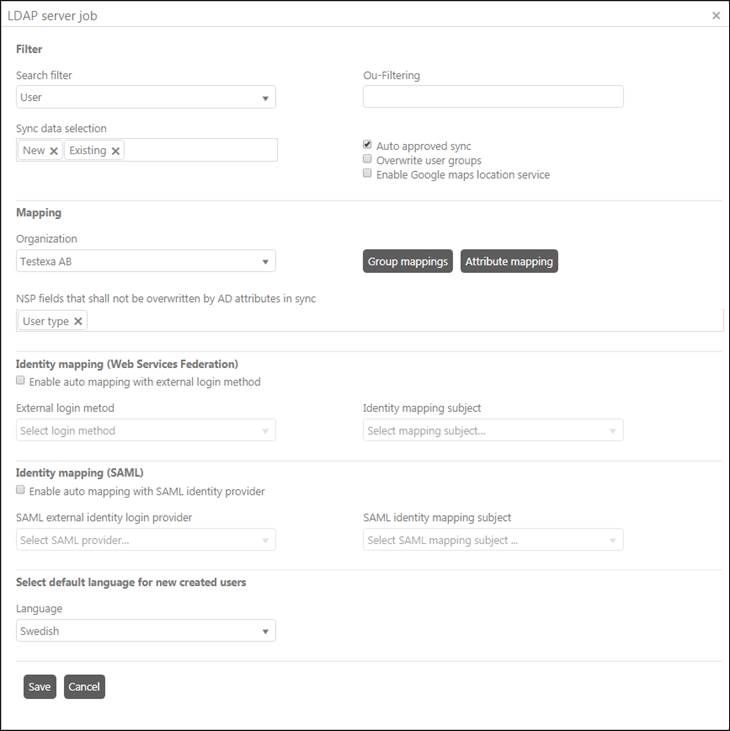
LDAP Server Job
Fields and buttons in the form are:
•Search Filter: Select search value to filter users of the Active Directory. Based on the value selected in this field, the users are filtered and synced with NSP. Two values are provided in the list: User and Organizational Unit. If User is selected then only users from the active directory are synced whereas if Organizational Unit is selected then all the OUs are fetched and synced with NSP.
•Ou-Filtering: Filters Organization unit. You can add organization units you want to fetch data from separated with semicolon. Example: ou = Sales; ou = Marketing. Read more here.
•Sync data selection: Select which data you want to fetch, new one, existing one, or both. If New is selected the synchronization will collect only new users of the Active Directory, in other words, those which are not in the NSP. If Existing is selected the synchronization will collect only users which already exist in NSP. If both options are selected, the synchronization will collect all users. All users will be collected also when nothing is selected.
•Auto approved sync: If not selected a record made by this job has to be later approved in Sync log page.
•Overwrite user groups: If this is checked, the sync will update NSP group membership to current data set in Active Directory. Example: If a user has been removed from a group in AD, then the user will be removed from the corresponding mapped group in NSP too, after the sync. If this is not checked you only update existing data.
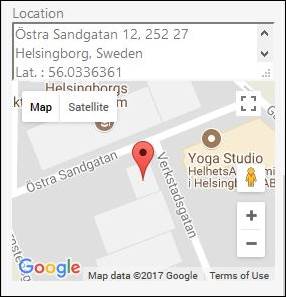
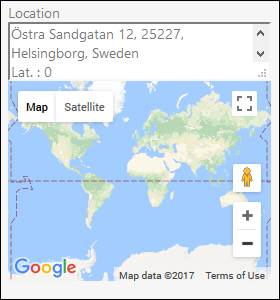
•Enable Google Maps location service: If enabled, system is using Google Map for locations. Longitude and Latitude is fetched from AD and converted to address by Google Maps service. This service could be switched off because the function uses Google Maps queries. Google Map services is free of charge for 2500 queries per day. Read more about Google Maps API Key.
View of user location with and without Google Maps location service:
•Organization: Select name of the organization to which the users will belong after synced with NSP.
•NSP fields that not shall be overwritten by AD attributes in sync: Select NSP attributes that shall never shall be overwritten (existing values in NSP shall be kept when sync from AD). Click in field to open a dropdown containing available attributes. Several attributes can be selected. Remove by clicking x.
•Group Mappings: This button will appear only when you Edit a LDAP Server Job. When you create a new Job you have to Save it once first and then Edit to be able to map groups. Click here to open a popup, where you map groups in Active Directory to corresponding groups in NSP. You have to map at least one group.
Note: If you specify a NSP group, but no corresponding AD group, all users in AD will be imported to the NSP group.
For more info on Group mapping, see example.
•Attribute mapping: The system comes with a standard mapping set up. If you want to make other mappings than default or to map AD properties that not are mapped by default, click here.
•Select default language for new created users: When a new user is created in NSP (from AD synchronization), the default language for the user will be set to this language.
Web Services Federation identity settings:
•Enable automatic mapping with external login: With this setting enabled NSP will make an automatic mapping from logged in user to NSP user. Mapping is done by subject defined in Identity mapping subject dropdown. If setting is not enabled users have to do the mapping to NSP user manually.
•Web Services Federation external login: Here you select which external login method shall use the automatic mapping. In dropdown you can select all defined login methods of type WsFederationIdentityProvider. Read more about external login methods here.
•Identity mapping subject: Select here which Active Directory subject shall be used to do the automatic mapping. Default is UserPricipalName. It is recommended to change from default only for special reasons and administrator has full control of the effects.
SAML identity settings:
•Enable automatic mapping with SAML identity provider: With this setting enabled NSP will make an automatic mapping from logged in user to NSP user. Mapping is done by subject defined in SAML Identity mapping subject dropdown. If setting is not enabled users have to do the mapping to NSP user manually.
•SAML external identity login provider: Here you select which external login method shall use the automatic mapping. In dropdown you can select all defined login methods of type SAML2. Read more about external login methods here.
•SAML Identity mapping subject: Select here which Active Directory subject shall be used to do the automatic mapping. Default is UserPricipalName. It is recommended to change from default only for special reasons and administrator has full control of the effects.
Note: If you use SSL connection on AD you must have digital certificate installed on IIS server for specific AD domain.